
Cybersecurity Detection Tool
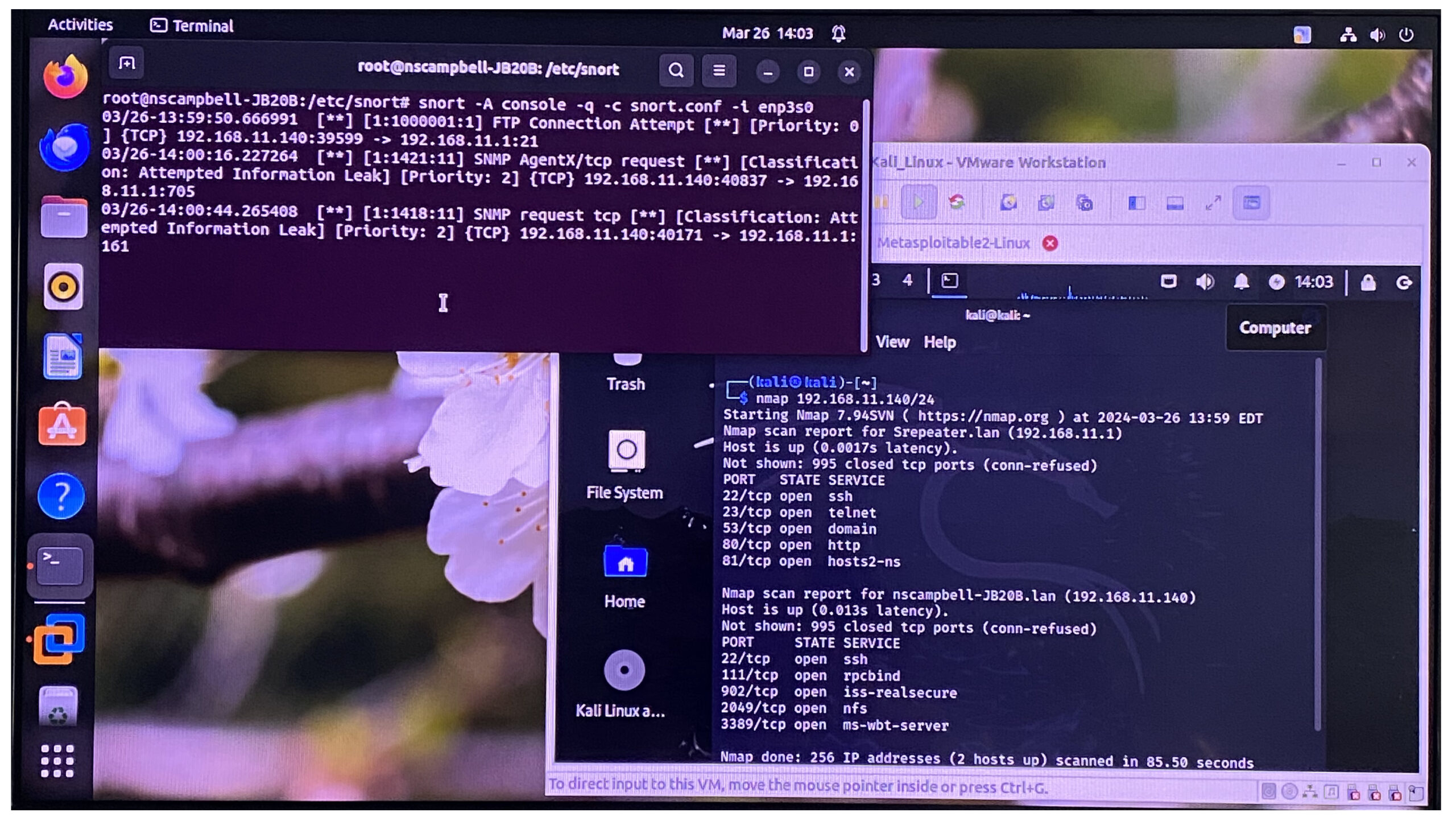
As I researched ideas on what to configure for my cybersecurity Homelab, I came across the project of building a detection tool for adversaries. I discovered cyberwoxacademy.org and the IDS that was suggested was Security Onion. I decided to use Snort instead because it’s an IDS and an IPS and it could be either host-based or network-based. After I installed Snort, I configured Kali on VMWare. Then I activated Snort by having it listen on the ethernet interface that is connected to my Wifi extender. Then, from Kali, I’ve done an Nmap. While Snort was listening on the Nmap, it shows results about an information leak to the default gateway of the network. Here is the image below. The command snort activates Snort, -A is for the display, "console" shows the output on the console, -q stands for "quiet" which filters out unnecessary information, -c allows me to choose a configuration path, -i specifies which interface to listen on, enp3s0 is the ethernet interface connected from the mini PC to the WiFi extender.
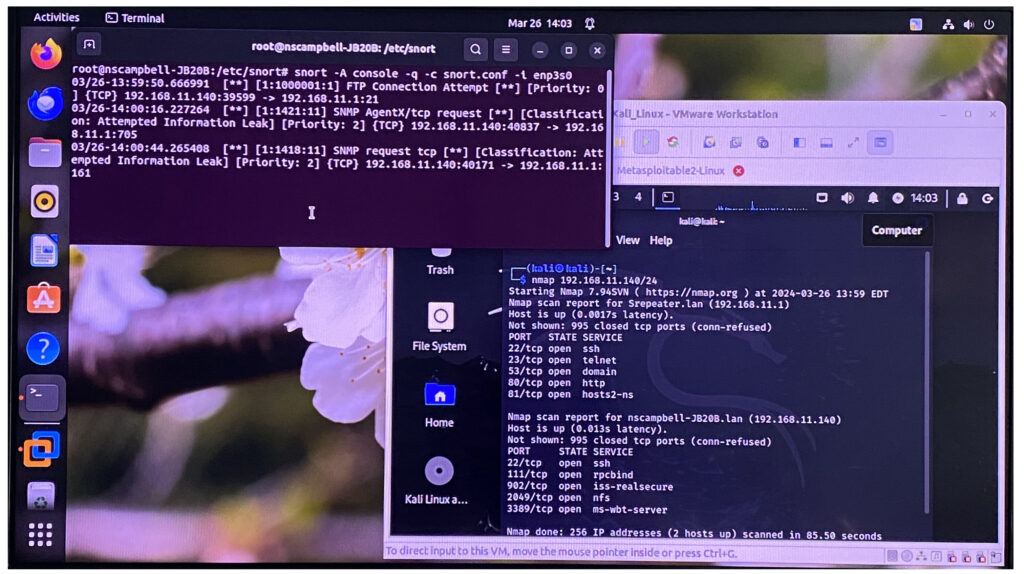
Since 192.168.11.1 is only the default gateway of the network. I've done more investigating using Zeek, which is a tool that reads packet capture files and breaks them down to become more readable for the human. It also gave me additional information on the malware analysis. Before I used Zeek, I wrote a packet capture file while Snort was listening for malicious traffic. In the image below I've done a tcpdump on the same ethernet interface Snort was listening on. In this tcpdump command the -s 0 will set the capture byte to its maximum so that I would gather all of the information from the packets. The -i refers to the interface and the -w allows me to write the packets on the file "traffic.pcap".
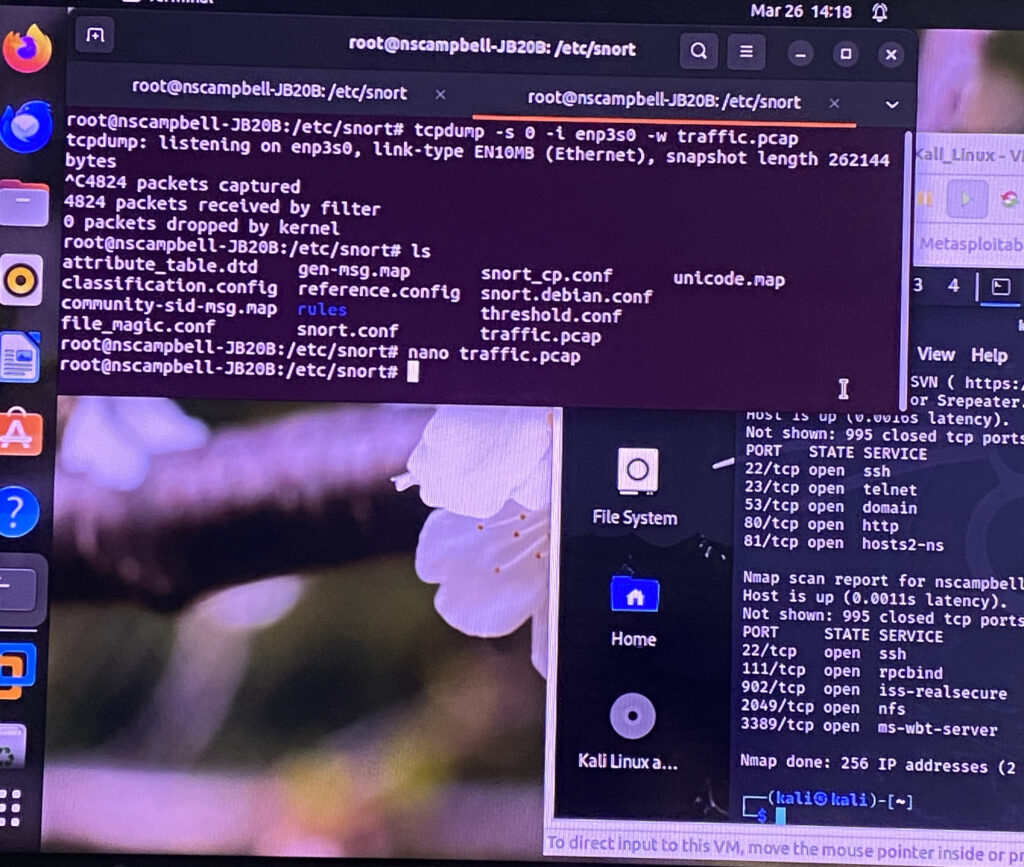
After I created the packet capture file, I made sure that Zeek is installed. Then I created a new folder in Downloads called "demo". From there, I had Zeek read the .pcap file and break them down into logs in to an empty folder. I wanted to see what contents are in conn.log.
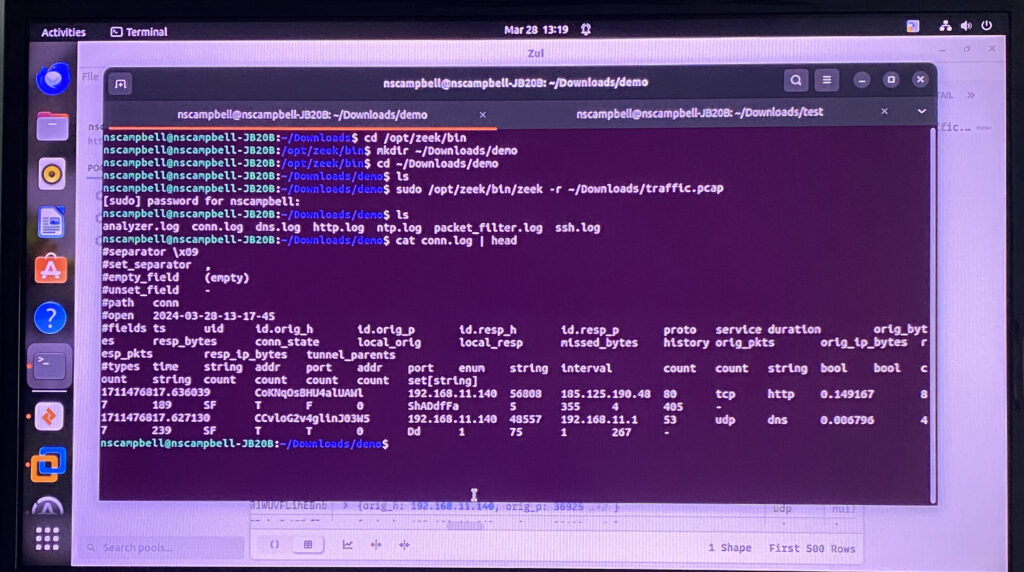
Since the output is a little hard to read, I installed "zeek-cut" so that I can only get the information I've chosen by header. So instead of doing "head", I've done "zeek-cut uid id.orig_h id.resp_h". In other words, I wanted to filter results showing only the user IDs, the source and destination ip addresses. Here's an example:
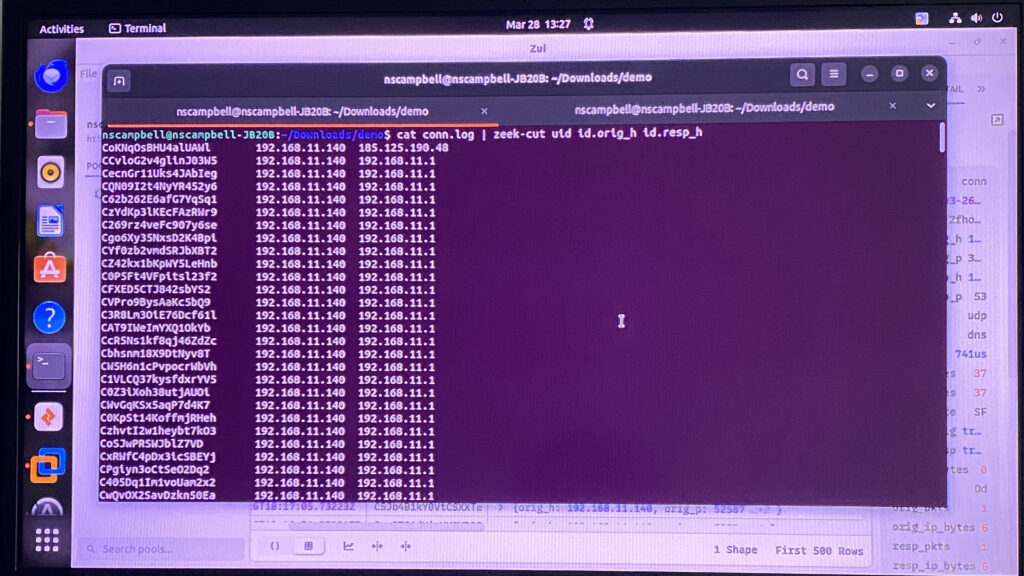
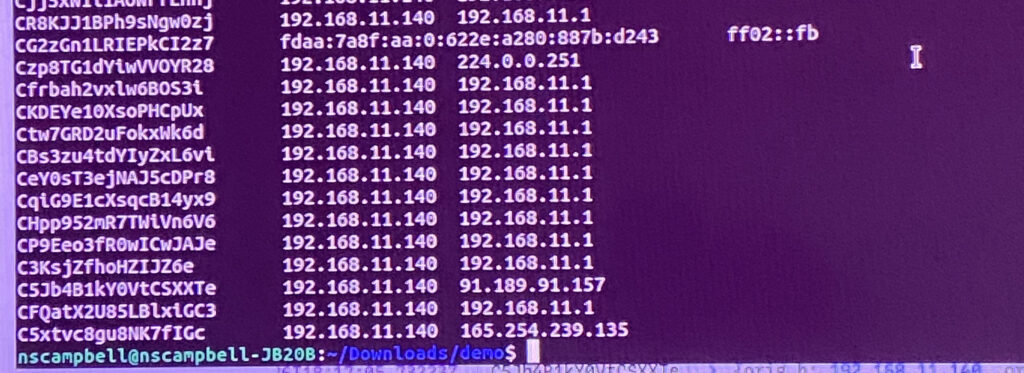 Here I've discovered four public IP address from the malware analysis. If this were to happen by an actual attacker I would know which IP address to block, instead of the same default gateway the client is already using.
Here I've discovered four public IP address from the malware analysis. If this were to happen by an actual attacker I would know which IP address to block, instead of the same default gateway the client is already using.